+Anil Anvesh
All these days we are browsing internet through browsers. There are many browsers available on the web. Today we are sharing a simple tip using which you can surf internet without any browser.
Tip to Surf Internet Without any Browser:
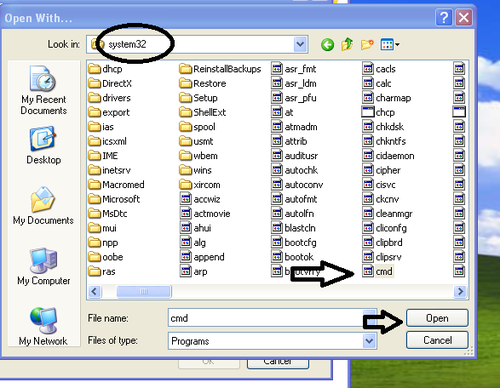
1. Open Run, type calc and hit enter as shown in below pic. It opens windows calculator.
2. In calculator click on Help and then click on Help Topics as shown in below pic
3. In calculator help window right click on Title Bar and then click on Jump to URL as shown in below pic.
4. A small popup window appears on the screen as shown in below pic, where you have to enter the url which you want to surf.
5. Finally after entering url hit enter. The requested website will appear in the side window of calculator help window as shown in below pic.
Note: If you want to browse another website follow the above steps 3 and 4. Type the full website address including http://
You May Also Like

















.jpg)

.jpg)
.jpg)